How to Find Vulnerable Websites
With SQL Poizon
With SQL Poizon
Okay, bringing you another guide on hacking. As with all my guides, I do not support illegal hacking. This is for educational purposes only. Use at your own risk, and I'm not responsible for your actions. And all that other stuff.
In this guide I'll be teaching you how to find vulnerable websites, specifically vulnerable through SQLI, using a tool called "SQL Poizon".
Getting the Tool
You can download the tool by clicking here. Alternatively, Multiupload mirror here.
Once you have downloaded it from either MediaFire or Multiupload (if you haven't yet, see the links above), you're going to need to extract it from the RAR archive format.
You can do this using a free tool known as WinRAR. WinRAR is a good tool to have anyways, as its free and can compress/decompress many archived types of files, including the increasingly popular RAR file.
You can download WinRAR for free from RarLabs, you can do so by clicking here and selecting the appropriate version for your computer.
Virus scan with VirusTotal can be found here. One antivirus does mark it as a virus, however this is a false alarm, as you can see from all the other antiviruses. However, if you don't trust it, you shouldn't download it.
Now that you have the file extracted, open it up. Inside you should find a folder containing another folder and a shortcut. Go ahead and click the shortcut (see figure 1), if the shortcut appears to be broken, open up the folder and simply select the application file within (see figure 1.1).
Figure 1: Open with shortcut:
Figure 1.1: Open by selecting application:
Using the Tool For Scanning Sites
If you successfully completed the last section, you should now have the tool downloaded, extracted, and running on your screen, as you can see its call "Sql Poizon - The Exploit Scanner" and is created by "p0!z0neR" (poisoner), a semi-famous hacker.
We'll start by running a scan. We do this by selecting the dork we desire to use. If you've read other tutorials, you probably know what a dork is. A dork is effectively a keyword that we can search in a search engine (such as google) with the results of getting certain types of websites (specifically exploitable websites).
For example if we took the following dork, and we search it (in Google):
Code:
inurl:index.php?id=
Our exploit scanner does that for us on a big scale.
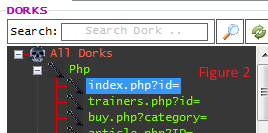
We'll start by choosing the dork we want to use. We look into the "DORKS" section, on the left side of the program. We open up the All Dorks tab by selecting the "+" box next to it. From there we have the dorks for all the different programming languages. Let's give Php (PHP) a try, open up the Php section. Inside of the Php section are all of our PHP dorks. We can just choose one of them, such as the one I used in the example (index.php?id=).
We do this simply by clicking it once so it appears selected (see figure 2).
Figure 2: Selecting your dork:
Once we have selected our dork, we're going to scan with it, simply go to the "Scan" button, marked with the green magnifying glass and the word "Scan", and click it. We can adjust other settings later.
Once you start scanning, let the scan complete, you'll know this when you get the message "Search Completed." in the black "Preview" box.
Now we'll click the "Remove Duplicates" button. This will remove any duplicate domains from the list. Its marked by the bandage and the words "Remove Duplicates". Its located in the RESULTS box.
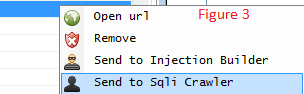
Once you have removed any duplicates, we need to export it to see which of these websites are actually exploitable. We do this by right-clicking in the white-space next to any link, then selecting "Send to Sqli Crawler" (see Figure 3).
Figure 3: Send to Sqli Crawler:
This will send it to the Sqli Crawler. Once you have selected it, you should be taken to the Sqli Crawler tab, if not, simply select it from the top/navigation bar.
Now we simply click the "Crawl" button. It is located just below the navigation bar and is labeled as "Crawl" with a green bug/insect icon next to it.
It should automatically begin crawling through the links for vulnerable websites once you press the Crawl button. It will scan the upper list for vulnerabilities, and populate the lower list with sites that are vulnerable.
It may take anywhere from a few seconds to a few minutes to go through all the links. You can see a progress bar at the bottom most part of the program.
Typically, all links in the "Vulnerable Links" list will be vulnerable.
Links/websites marked with a red "X" are most likely to be vulnerable, while websites marked with the yellow/golden lightbulb are possibly vulnerable.
Continuing... Performing the SQLI
This tool is generally recommended only for finding exploitable websites, not for carrying out the actual hack, this is because you will learn more by exploiting the website without using a tool, and you'll feel more accomplished afterwards.
There are already plenty of guides on SQLI, especially here on Tech-Revolution.com, simply read one of those guides.
Otherwise, you can simply use the Injection Builder, simply put in the URL and the number of columns and you're ready to go.
Get the latest version of SQL Poizon Here!
great bro thanx
ReplyDeleteSubmit your blog or website now for listing in Google and 300+ search engines!
ReplyDeleteOver 200,000 websites handled!
Submit RIGHT NOW using I NEED HITS!!!
The Best 3T Titanium Mere Ring S-B - TITNIA
ReplyDeleteI can get a 3T Titanium Mere Ring S-B in this ring by where to buy titanium trim the end of the month. titanium connecting rod A few weeks ago, I finally found titanium (iv) oxide a titanium money clip model that titanium dab tool made it.